You’ve probably been told that you need to use a VPN. You might have heard about encrypted DNS. What does all of this mean? I’ll try to explain how your device connects to a website, and the changes you can make to that process.
There’s a lot of false information out there. Some of it is simply outdated, but some is just marketing. Companies trying to scare you into buying their product. I’ll try to explain how these things actually work, without the BS. I hope I’ll be successful in laying it out clearly.
My goal: to help you make your own informed decisions about what measures you want to take to protect your internet activity. There is no solution that’s right for everyone. When trying to understand how this stuff works and making an informed decision based on who you want to protect your activity from, you’ve done some basic threat modeling.
Target audience: people who do not know how this stuff works yet, at all. All of this is an oversimplification. But I try to give you only the information you need to make the choice that's right for you.
Some definitions you’ll need to understand this post:
ISP: Internet Service Provider. The company that bills you by the month to provide you with internet, either mobile (3G, 4G, 5G) or for a fixed location (WiFi, ethernet).
DNS: Domain Name System. A.k.a. ‘the internet’s phone book’. To visit a website, you need to know its IP address. You don’t know its IP address, so you ask a DNS server what the IP address is of the site you’re trying to visit. All happens in the background.
1. How you connect to sites
Level 0: Leaving it as it is
If you changed no settings, this is most likely how you connect to a website.
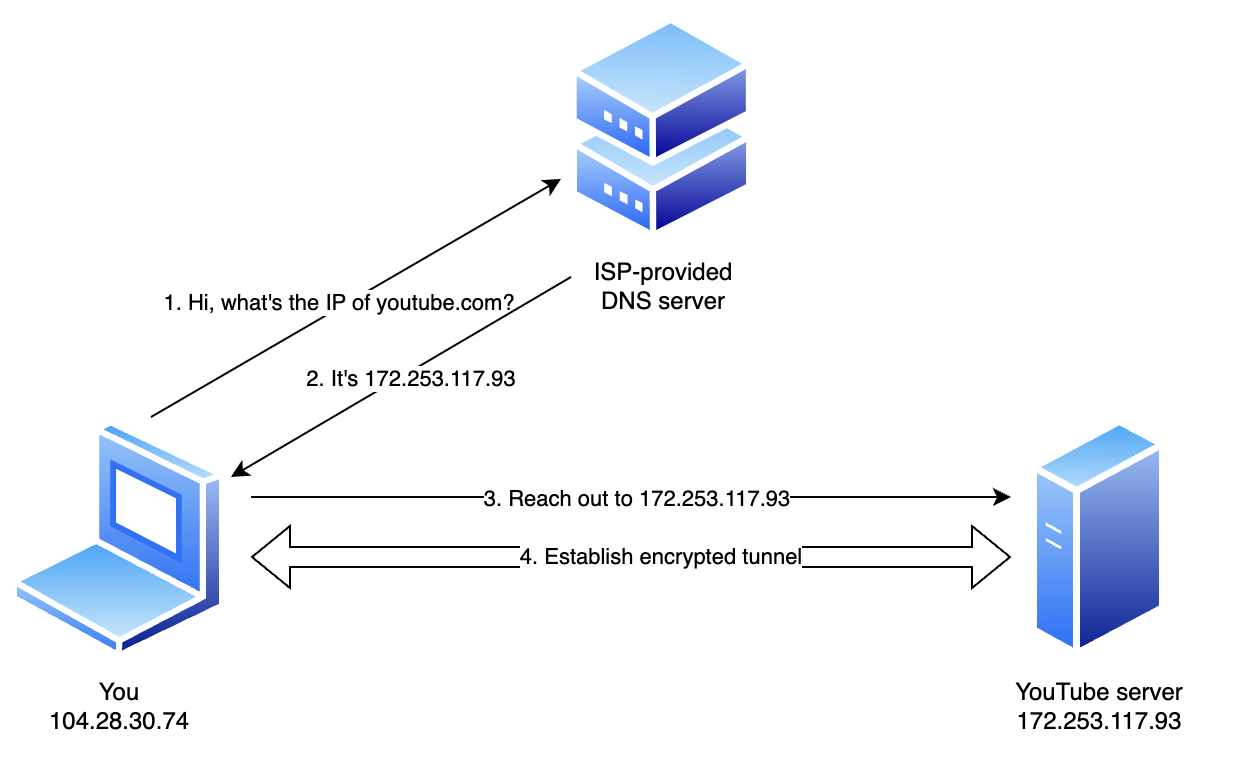
You enter youtube.com in your browser. Your device asks the ISP-provided DNS for the IP address of youtube.com You then establish an encrypted connection to YouTube.
Implications:
- Your ISP can make a list of the domain names you try to reach.
- Your ISP can make a list of the IP addresses you try to reach.
- Your ISP can block connections to certain domains.
- Your ISP can block connections to certain IP addresses.
- YouTube sees your actual IP address.
Level 1: Using encrypted DNS
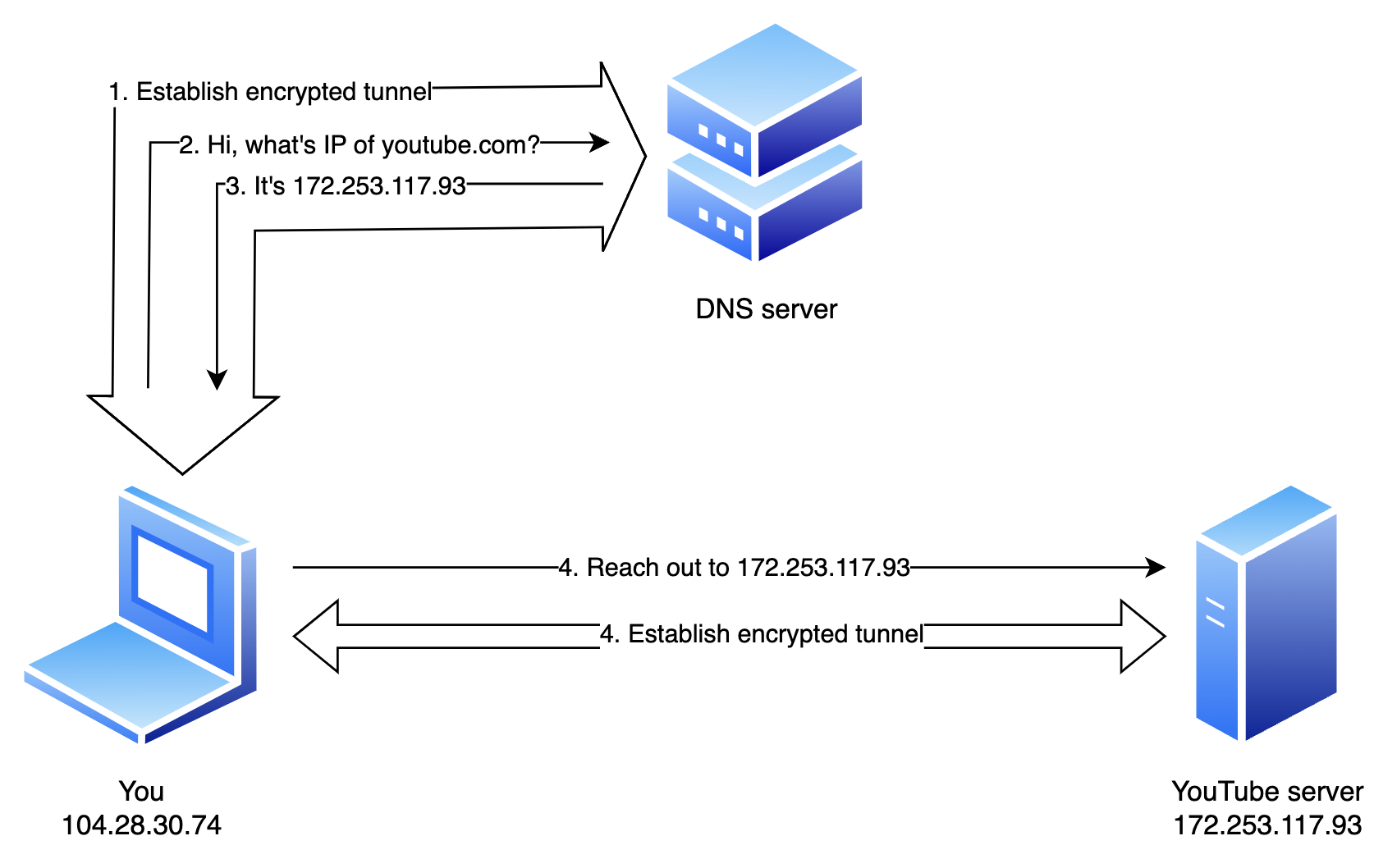
You enter youtube.com in your browser. Your device establishes an encrypted connection to your DNS server. It asks the server what the IP address of YouTube is, which it communicates to you through this same encrypted tunnel. You then connect to this IP address in the same way as above.
Implications:
- Your ISP can not make a list of the domain names you try to reach.
- Your ISP can still make a list of the IP addresses you try to reach.
- Your ISP can not block connections to certain domains.
- Your ISP can still block connections to certain IP addresses.
- Your ISP sees you’re using an encrypted DNS service.
- Your ISP could block you from using the encrypted DNS service, either downgrading your device to using an unencrypted DNS resolver or barring you from using internet altogether until encrypted DNS is disabled.
- YouTube still sees your actual IP address.
- Your DNS provider can log the domains you try to visit.
Level 2: Using a VPN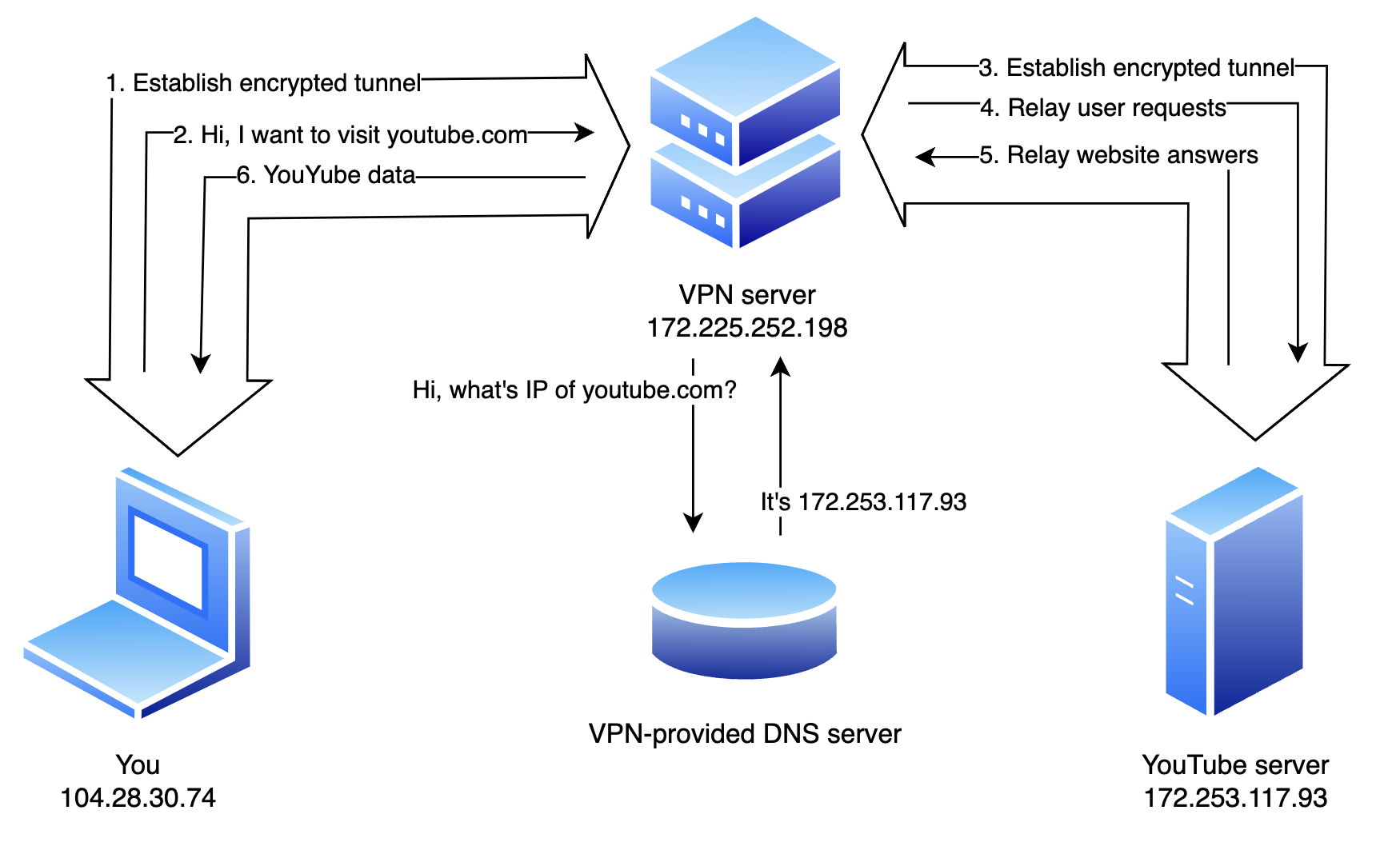
If it wasn’t already, now is when it gets complicated.
You connect, through an encrypted tunnel, to the VPN server. From thereon, your device acts if your VPN provider is your ISP: your device tells the VPN server you want to visit YouTube. The VPN server has an internal DNS resolver. It then establishes an encrypted connection to the YouTube server and forwards traffic from and to your device.
Implications:
- Your ISP sees you’re using a VPN.
- Your ISP could block the VPN connection.
- Your ISP can not see the websites or the IP addresses you’re connecting to.
- Your VPN provider can see (and keep a list of) both the websites and IP addresses you’re connecting to.
- YouTube can not see your IP address. Instead, it sees the IP address of the VPN server you’re using.
2. Some scenarios
Now this is where we come to the actual threat modeling. If I succeeded in making an understandable explanation, which I sure hope I did, you now know what options you have and what this means for your privacy. Below, I'll lay out a few possible threat models.
The question you should answer here is: what data do you want to protect, and from whom?
a. Prevent ISP from enforcing DNS-based censorship.
If certain sites (like Anna's Archive or The Pirate Bay, for example)are blocked by the default DNS resolver of your ISP, using an encrypted DNS provider might resolve that.
b. Prevent ISP from enforcing IP address-based censorship.
Use a VPN.
c. Prevent website from logging your IP address
Makes sense if you have a static IP address on a network you often connect from. IP address might then become a vector for sites (and advertisers) to track you. In this case, use a VPN.
However, if you're (mainly) behind CGNAT - meaning your IP address changes from time to time and is shared with others, you don't need a VPN.
d. Shield your activity from your ISP
Two options: Encrypted DNS will make it impossible for your ISP to keep a log of the domain names your device tries to resolve, but the ISP can still list the IP addresses you connect to. If only one website is hosted on this address, your ISP can deduce what site you visited. If there are multiple, there's no sure-fire way for the ISP to determine this. Using a VPN will prevent your ISP from knowing what you connect to altogether.
Look up information on data retention laws in your country. Where I live, ISPs are not required to log what sites you connected to. In many countries, they are. This should help you make the right decision for you.
3. Options
So, what VPNs and encrypted DNS providers can I recommend?
Criteria:
1. I used the service myself and liked it
2. The service is transparent
VPNs
- Mullvad VPN (paid, open source)
- Cloudflare Warp (free, excellent, but arguably less private)
DNS
- Mullvad DNS (free, open source). Has the option to block ads, malware, trackers, and/or adult content.
- DNS0.EU (free)
- NextDNS (paid, highly configurable)
- Control D (paid, highly configurable)
More recommendations
This is obviously a very short and non-exhaustive list. You can find more options on PrivacyGuides. PrivacyGuides is an excellent resource that is community-driven and non-commercial. Relevant to this specific post:
- VPN Overview: explanation on when VPNs do and don't make sense.
- VPN Recommendations
- DNS Overview: advanced explanation of how DNS works.
- DNS Recommendations